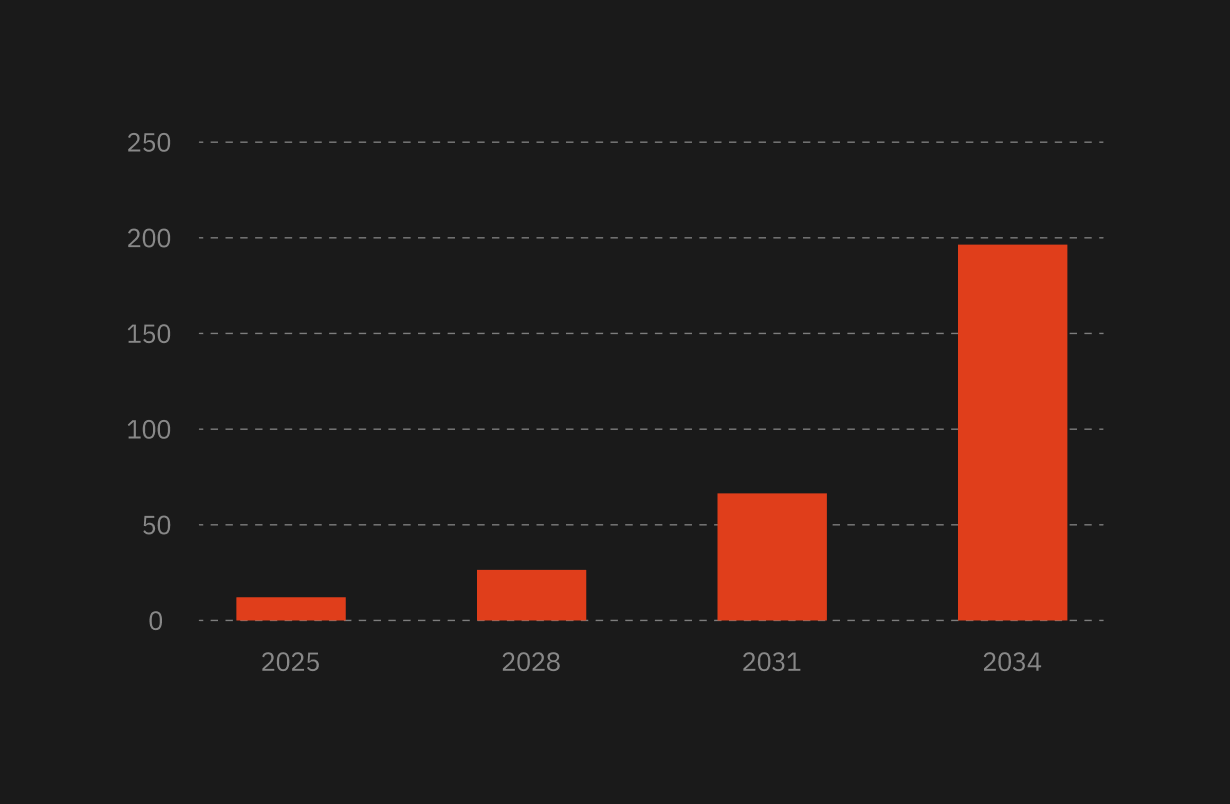
As of 2023, the average data breach cost an organization nearly $10 million. For many small businesses, that's a mind-blowing amount that could spell disaster. Not having proper software security is like leaving your front door wide open — an invitation for trouble. But let's face it, not every company has a cybersecurity superhero on standby, nor the budget to hire one.
This handy guide offers a straightforward roadmap to beef up your software's defenses against common security risks using resources at your disposal.
Security Testing in the Software Development Life Cycle (SDLC)
Security testing should be conducted throughout the software development lifecycle to ensure the final product is secure. Depending on the outcome of various tests, the team will need to make adjustments and updates to the software to ensure it is secure and guarded against potential risks.
Requirements:
- Security Analysis: Begin by identifying and defining security requirements. This involves understanding what security measures need to be in place and exploring potential security risks that should be addressed from the outset.
Design:
- Security Test Plan: Develop a comprehensive security test plan during the design phase. This plan should outline the methods and timing for conducting security tests, ensuring that security is built into the design rather than added later.
Coding & Unit Testing:
- Security White Box Testing: Conduct thorough internal testing using white box techniques. This involves leveraging detailed knowledge of the internal structure of the application to identify and fix security vulnerabilities early in the development process.
Integration Testing:
- Security Black Box Testing: Perform black box testing by employing testers who do not have prior knowledge of the system's infrastructure. This approach helps simulate real-world attack scenarios and identifies vulnerabilities that might be overlooked by those too familiar with the system.
System Testing:
- Vulnerability Screening: During system testing, evaluate the system for potential risks, including bugs, weak passwords, and immature network protocols. This comprehensive screening helps ensure that all parts of the system are secure before deployment.
Deployment:
- Penetration Testing (Pen Testing): Conduct simulated attacks to assess the system's vulnerabilities and risks. Pen testing helps identify potential security breaches and areas for improvement before the system goes live.
Support:
- Impact Analysis of Patches: After deployment, continually evaluate the impact of patches on the system's security. This involves assessing how updates and changes affect the overall security posture, ensuring that patches do not introduce new vulnerabilities.

White Box vs. Black Box Security Testing
White box and black box are two valuable types of security testing to conduct throughout the software development cycle. White box security testing is conducted by testers with an intimate knowledge of the system infrastructure. These testers leverage this knowledge to conduct their testing and evaluate risks in the coding, design, and infrastructure.
When it comes to black box security testing, testers do not have an understanding of the system’s internal workings. This is similar to the knowledge potential hackers would have when attempting to infiltrate a system. It focuses primarily on user experience and behavior to identify risks and gaps. While black box testing is most similar to real-world attacks, this approach may miss internal vulnerabilities and is limited by the tester’s creativity.

White box testing is known for being more thorough and detailed, making it possible to identify hidden vulnerabilities. White box testing is typically conducted earlier in the software development process, but black box security testing can be done on an ongoing basis.
What are Common Web Application Security Risks?
There are many common security risks for web applications. Familiarizing yourself with common security threats can boost your application’s safety. According to the Open Web Application Security Project (OWASP), the following are the top ten common web application security risks from 2021, many of which have repeatedly ranked in the top ten for several years.

A01-Broken Access Control
Access control enforces a policy that ensures users cannot act outside of their intended permissions. Broken access control typically leads to unauthorized information disclosure, modification, or destruction of all data or performing a business function outside the user's limits.
How Can You Defend Against Broken Access Control Risks?
- Search your code, application, and metadata to ensure no secret data (such as documents or access codes) is disclosed.
- Implement access control mechanisms once and re-use them throughout the application, including minimizing Cross-Origin Resource Sharing (CORS) usage.
- Ensure only account owners have permission to change their data.
A02-Cryptographic Failures
Lack of encryption leads to cryptographic failures, wherein sensitive data is wrongfully exposed via plain text. Any data that falls under GDPR or is particularly sensitive (such as business secrets) should be encrypted to reduce the risk of exposure.
How Can You Defend Against Cryptographic Failures?
- Be sure to encrypt confidential data.
- Do not use protocols without encryption.
- Do not store unnecessary data longer than required.
A03-Injection
During an injection attack, a hacker inputs data to harm the host system. These attacks can be substantially dangerous, leading to data loss, corruption, or the loss of control of the host system. As a well-known, established hacking technique, there are many tools even inexperienced hackers can leverage to take advantage of these vulnerabilities.

How Can You Defend Against Injection Risks?
- Use a secure framework to process user input (Alchemy).
- Use "whitelist" and "blacklist" on the server side.
- Input sanitization for dynamic prompts.
- Use frameworks that automatically exclude the possibility of using XSS.
A04-Insecure Design
Insecure or immature design can allow hackers to bypass authentication, mine sensitive data, modify URL parameters, and more. Insecure design is a broad category with significant risks. Early testing during the development process is vital for combatting potential insecure design risks.
How Can You Defend Against Insecure Design Risks?
- Establish and operate a secure development lifecycle with AppSec professionals.
- Create and use a library of secure design patterns.
- Use threat modeling for critical authentication.
- Integrate plausibility checks (from external interface to internal).
A05-Security Misconfiguration
Properly configuring your security settings can help you avoid many common vulnerabilities. One key risk of security misconfiguration is leveraging default settings, which can make your system extremely vulnerable. Be sure to check your site's robot.txt file, as it contains a lot of information about pages that should not be indexed. Also, check whether access to these pages is protected by a corporate VPN.
How Can You Create a More Secure Password?
Ensure your password meets the following criteria:
- Is at least 15 characters, do not set a limit for password length
- Includes a password passphrase, which leverages a string of phrases instead of one word
- Random — do not create a variation of the default password (ie. Passw0rd, p@ssword, pa$$word)
- Private — ensure only those who need access have access
- Unique — do not reuse passwords
- Never use default passwords or usernames
How Can You Defend Against Security Misconfiguration Risks?
- Minimize the platform and remove unnecessary functions and components.
- Update components with known vulnerabilities.
- Do not use default settings.
A06-Vulnerable and Outdated Components
Vulnerable and outdated components are another common security risk. You are likely vulnerable if:
- You do not know the versions of all components you use (both client-side and server-side). This includes components you directly use as well as nested dependencies.
- The software is vulnerable, unsupported, or out of date. This includes the OS, web/application server, database management system (DBMS), applications, APIs and all components, runtime environments, and libraries.
- You do not scan for vulnerabilities regularly and subscribe to security bulletins related to the components you use.
- You do not fix or upgrade the underlying platform, frameworks, and dependencies in a risk-based, timely fashion. This commonly happens in environments when patching is a monthly or quarterly task under change control, leaving organizations open to days or months of unnecessary exposure to fixed vulnerabilities.
- Software developers do not test the compatibility of updated, upgraded, or patched libraries.
- You do not secure the components’ configurations).
How Can You Defend Against Vulnerable and Outdated Components?
- Only obtain components from official sources over secure links.
- Continuously inventory the versions of both client-side and server-side components (e.g., frameworks, libraries).
- Monitor for libraries and components that are unmaintained or do not create security patches for older versions.
- Use the following resources to monitor for new vulnerabilities: some text
A07-Identification and Authentication Failures
Confirmation of the user's identity, authentication, and session management is critical to protect against authentication-related attacks, such as brute force attacks, session hijacking, and rainbow tables-related risks.
Brute force is a method used in cryptography and cybersecurity to crack passwords or encryption keys by systematically trying all possible combinations until the correct one is found. This is time-consuming for hackers, more so if you use a secure password. Multi-factor authentication, lockout mechanisms, and CAPTCHA can minimize the risk of brute force attacks.
Session hijacking, or cookie hijacking, is a hacking method involving the exploitation of a valid user session. An attacker can take over the session by masquerading as the authorized user to access their personal information and passwords.
Rainbow tables are a type of precomputed table used in cryptanalysis and password cracking. They are designed to accelerate the process of reversing cryptographic hash functions, particularly those used to store passwords in a hashed format.
How Can You Defend Against Identification and Authentication Failures?
Brute Force
- Encourage users to create strong passwords that are long, complex, and difficult to guess.
- Implement account lockout mechanisms that temporarily lock user accounts after a certain number of failed login attempts.
- Integrate CAPTCHA into login forms to verify that the user is a human and not an automated script.
- Implement multi-factor authentication (MFA) to add an additional layer of security beyond passwords.
- When encrypting sensitive data, use strong encryption algorithms and keys with sufficient length and complexity to resist brute-force attacks.
Session Hijacking
- Add session expiration date and confirmation of session creation.
- All sessions must be stored server-side.
- Clear cookies in the session without waiting for cookies expiration.
- When logging out of the user, kill the session.
Rainbow Tables
- Use multi-factor authentication.
- Do not send passwords and confidential data in the URL.
- Use the Secure and Http_only flags.
- Use industry-standard, up-to-date password hashing algorithms.
A08-Software and Data Integrity Failures
Software and Data Integrity Failures is a vulnerability that allows through serialization/deserialization to get privilege escalation and allow an attacker with admin rights to use the system. The attacker intercepts the object (token, cookie, session), parses it, and looks at its components. Then changes the admin rights and sends it to the server.
How Can You Defend Against Software and Data Integrity Failures?
- Use digital signatures or similar mechanisms.
- Make sure libraries and dependencies, such as npm or Maven, use trusted repositories.
- Ensure that a software supply chain security tool such as OWASP Dependency Check or OWASP CycloneDX is used.
- Ensure that unsigned or unencrypted serialized data is not sent to untrusted clients without any integrity check or digital signature.
A09-Security Logging and Monitoring Failures
In many companies, there are no logs or they do not have the necessary information, so no one knows the attacker's action.
Typical mistakes include:
- Lack of incident response plan.
- Uninvestigated incidents.
- Lack of event collection infrastructure.
- Lack of information about assets and documentation.
- Tampering with evidence.
- Provocation of the intruder.
- Unlearned lessons.
- Intruder notifications.
How Can You Defend Against Security Logging and Monitoring Failures?
- Ensure that all critical access control points and server-side authentication failures can be logged with sufficient context to identify suspicious accounts. And also enough time is kept.
- Create effective alert monitoring to detect and respond to suspicious actions in a timely manner.
- Create or adopt an incident response and recovery plan such as NIST 800-61 rev 2.
A10-Server-Side Request Forgery
Server-Side Request Forgery (SSRF) is a type of security vulnerability that occurs when an attacker tricks a web server into making requests on its behalf. The metadata of a cloud server such as AWS provides a REST interface where important configuration and sometimes even authentication keys can be retrieved.
How Can You Defend Against Server-Side Request Forgery?
- Segment remote access functionality across separate networks to reduce the impact of SSRF.
- Apply firewall policies.
- Validate all input provided by the client.
- Enforce URL, port, and destination scheme with a positive whitelist.
Top 5 Tools for Basic Security Checks
Even without specialized security expertise, the software team can leverage various tools to perform essential security checks:

Burp Suite Professional
Burp Suite Professional is your Swiss Army knife for web security testing, offering a comprehensive set of tools to identify vulnerabilities, ensure data protection, and enhance overall security measures for your web applications.
How to Use It:
- Set up a proxy to intercept and analyze HTTP requests.
- Use the scanner to identify common vulnerabilities.
- Automate repetitive tasks with Burp’s extensions.
Exploit Database (EDB)
Exploit Database (EDB) is a repository of exploits and vulnerabilities.
How to Use It:
- Search for known vulnerabilities related to your software components.
- Use this information to patch and secure your applications.
Metasploit Framework
Metasploit Framework is a powerful tool for penetration testing.
How to Use It:
- Simulate attacks to identify weaknesses in your system.
- Use exploits from the database to test the resilience of your defenses.
Nmap
Nmap is a network scanning tool.
How to Use It:
- Scan your network to identify open ports and services.
- Ensure that unnecessary ports are closed and services are secured.
Ettercap
Etter cap is a network security tool for man-in-the-middle attacks.
How to Use It:
- Monitor and analyze network traffic.
- Test your network’s resilience to eavesdropping and data interception.
Securing Your Software Without Breaking the Bank
Securing your software doesn’t necessarily need a dedicated cybersecurity specialist. With these strategies and tools, you can protect your business from costly data breaches. Remember, your customers, partners, and employees count on you to keep their data safe.
Ready to take the next step? Book a call with one of our experts at MEV. Our team is here to help you fine-tune your security strategy and pick the best tools for your needs.



.jpg)
.gif)


.png)
.jpg)
.webp)