In the previous part of this series, we explored the key features of AWS Config and its role in maintaining compliance. [LINK TO PART 1]
Now, we'll walk through the practical setup of AWS Config. You'll learn how to enable it, configure managed and custom rules, use Conformance Packs, and leverage Aggregators to manage compliance across multiple AWS regions and accounts. By the end, you'll have a clear understanding of how to implement continuous compliance with AWS Config.
AWS Config Setup
Step 1: Create an AWS account
First things first - you need to have an AWS account to perform all the actions. Follow AWS’s step-by-step guide to set one up.
Step 2: Enable AWS Config in the console
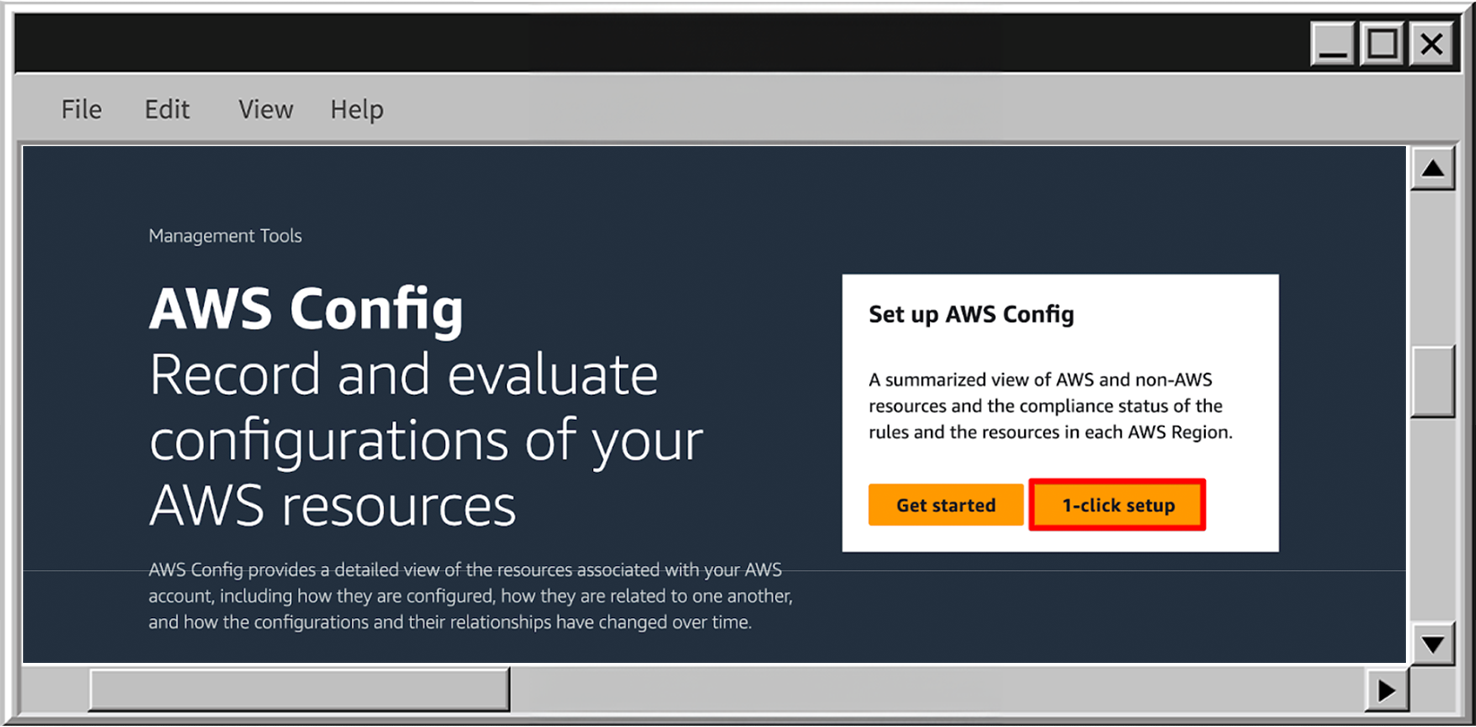
In AWS Console go to the AWS Config service and click on 1-click setup. By selecting this, AWS will automatically:
- Create all necessary AWS resources for you, including AWS IAM service roles and S3 bucket for configuration records.
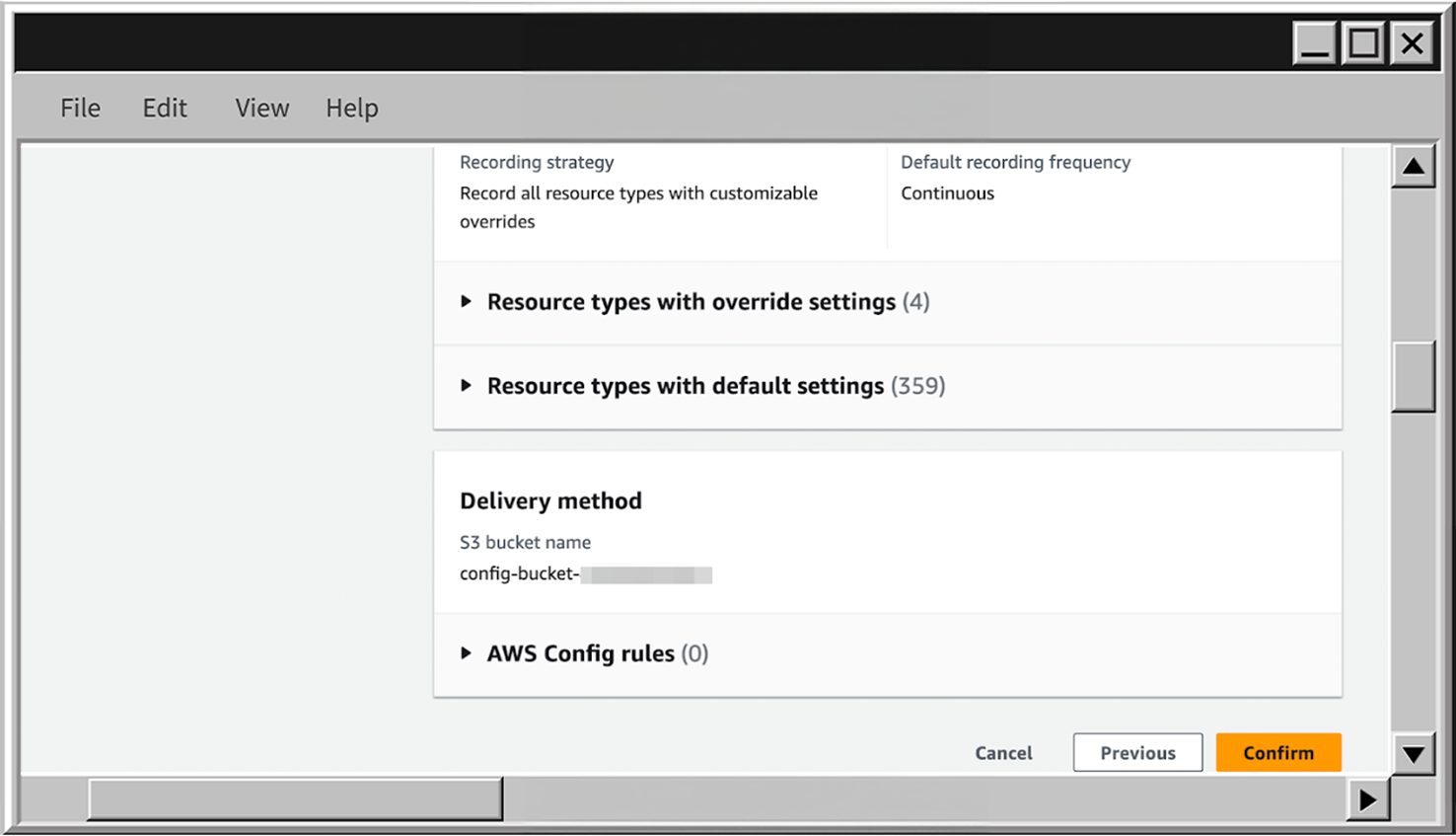
- Configure AWS Config Recorder to continuously track the configuration for all resources – except for AWS IAM.
Configure AWS Rules
Managed AWS Config Rules
AWS offers a vast library of predefined AWS Config rules. Let’s set up one.
- In the AWS Config go to the Rules section and click on Add rule.
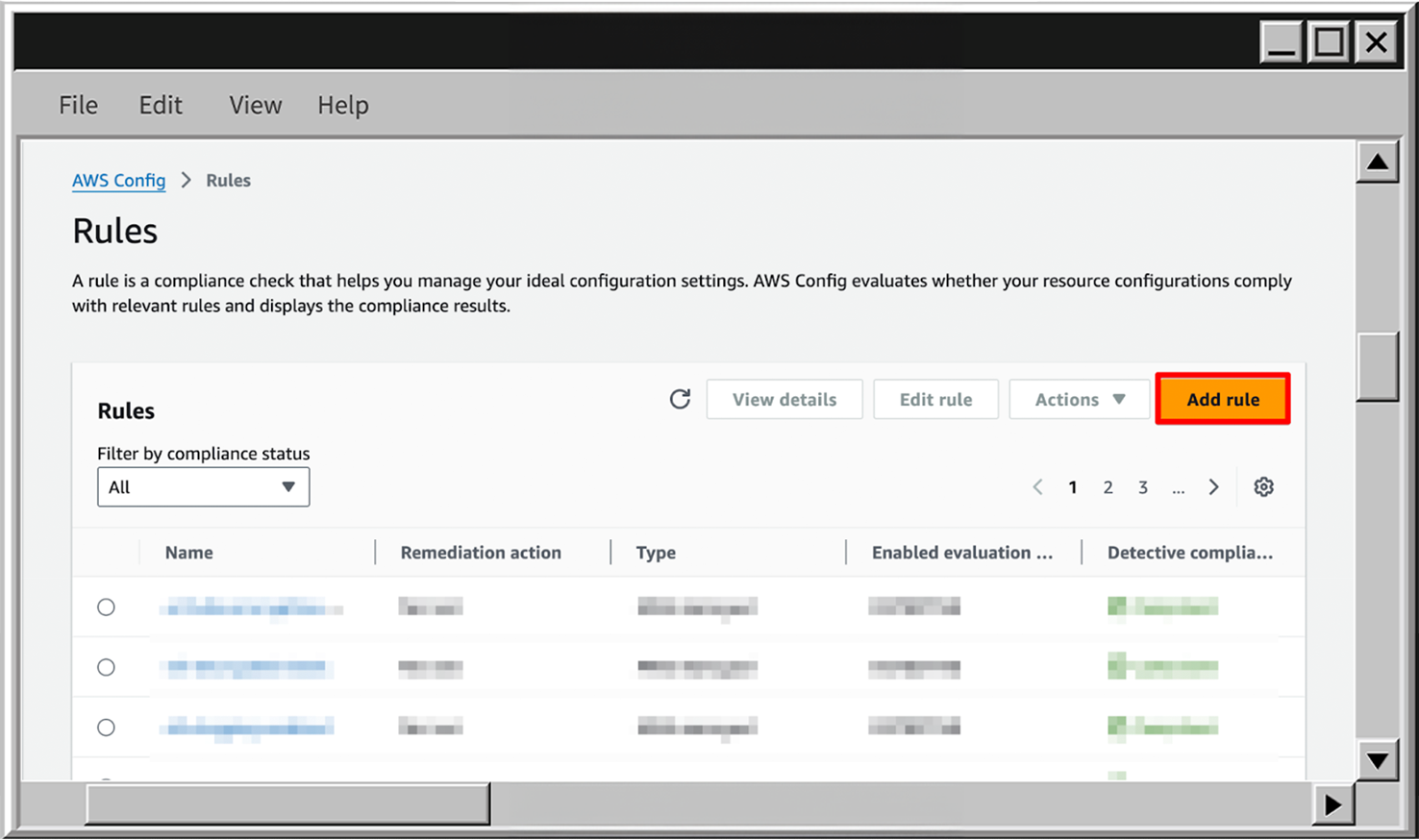
- Choose the AWS managed rule type and one of the EC2 rules - ec2-instance-managed-by-systems-manager to ensure that all EC2 has an AWS Systems Manager agent configured to have the ability to centrally manage them via AWS SSM.
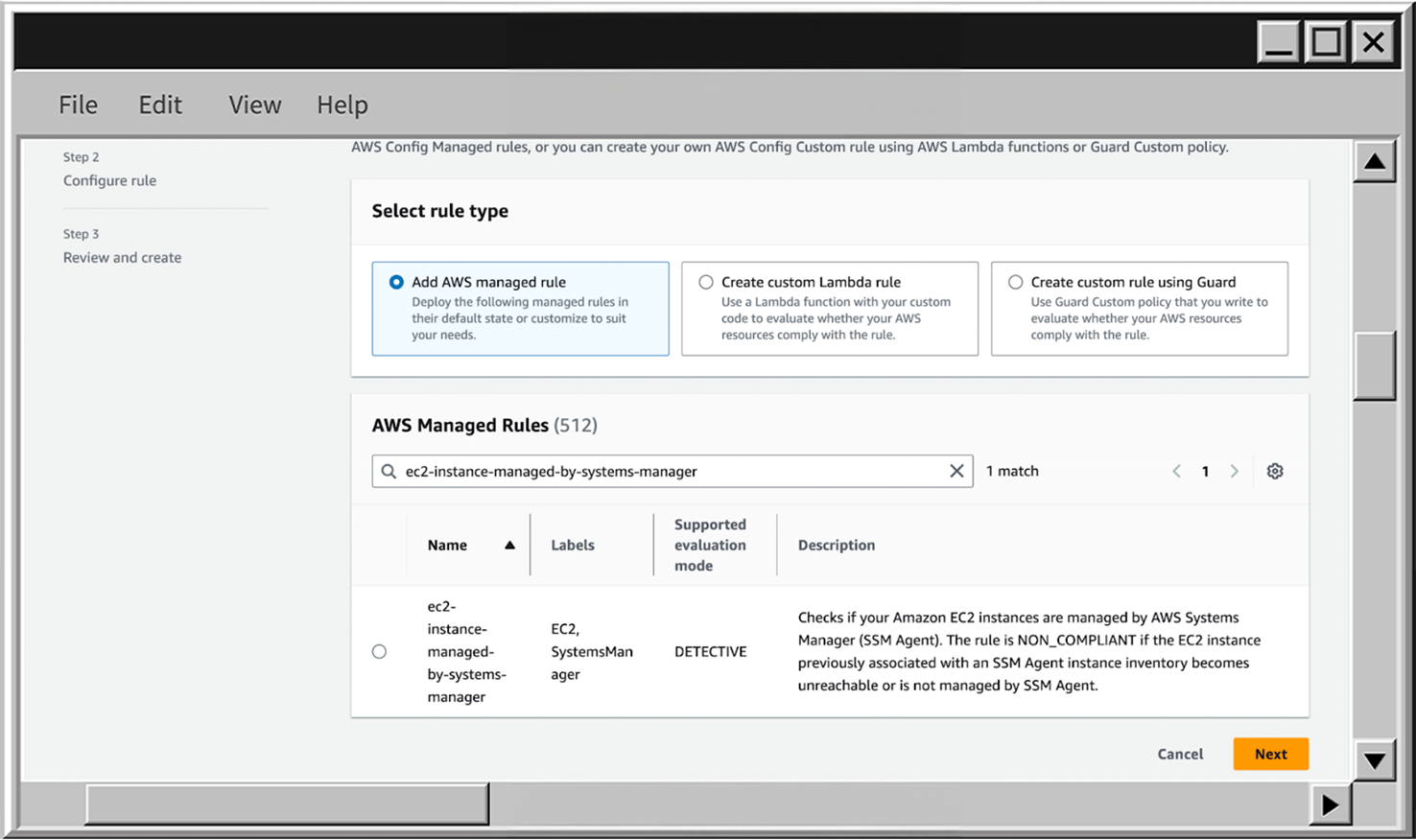
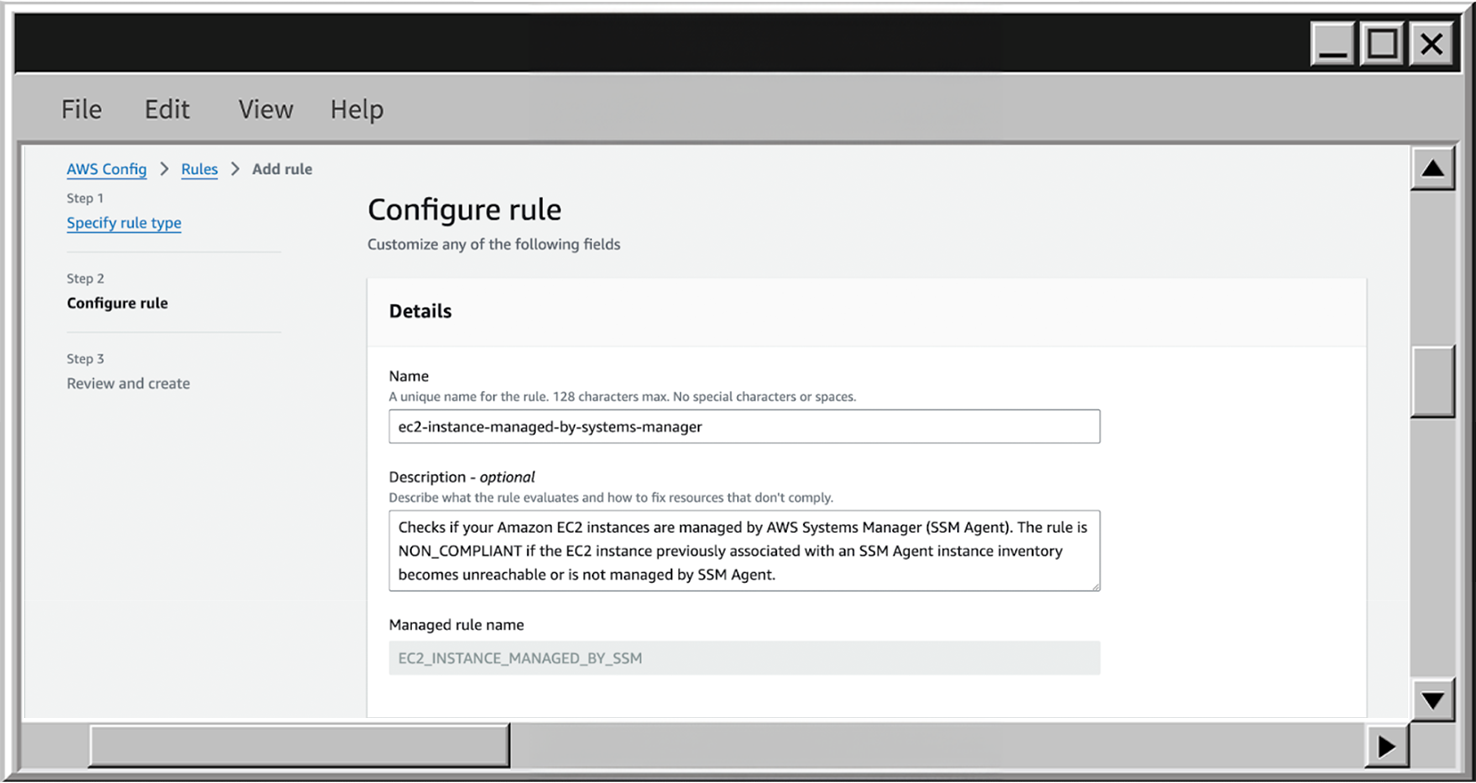
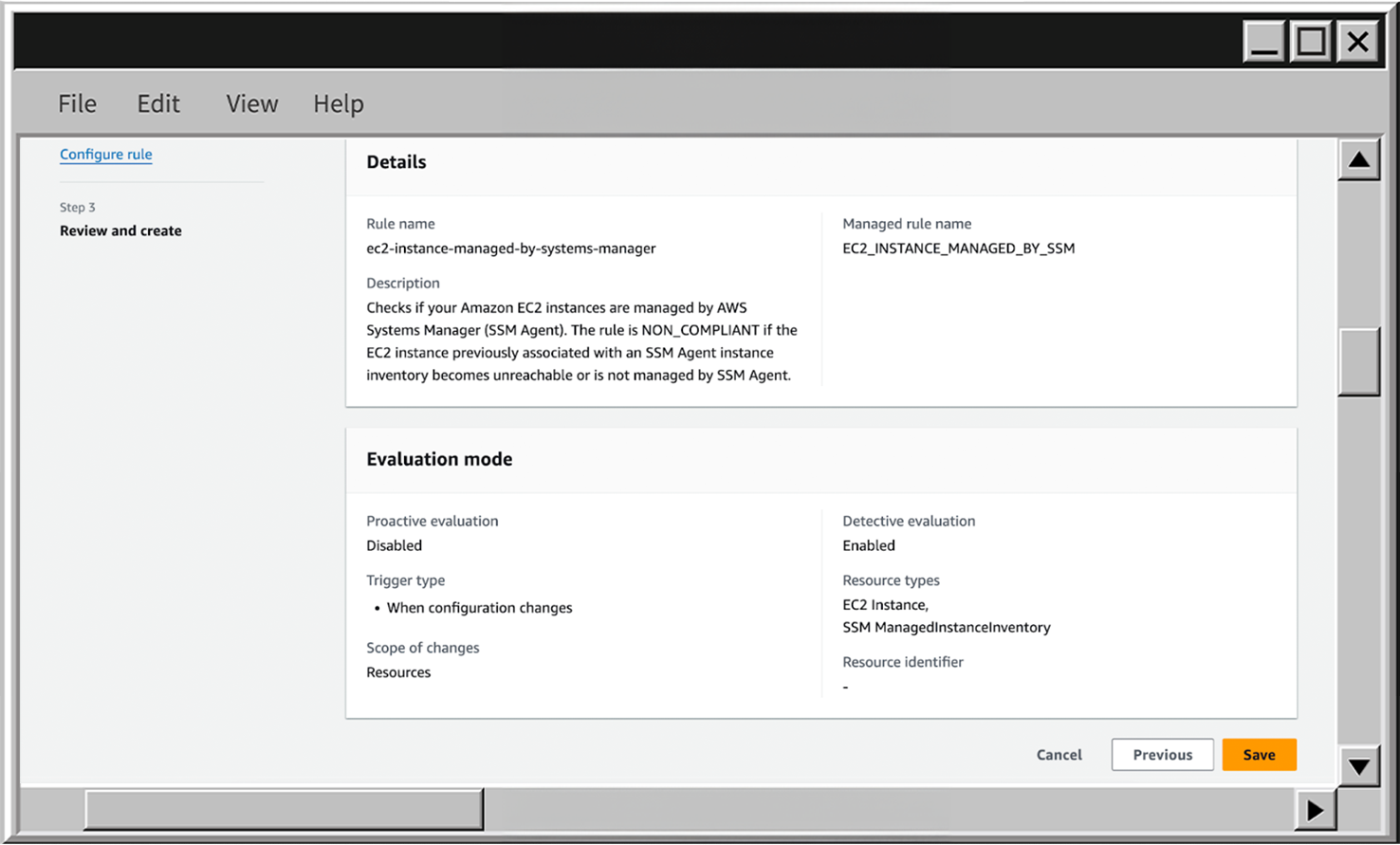
- When your first rule is created, you can find it in AWS Config to review the details by clicking on the View details button.
- On the details page you see the description, eligible resource type, evaluation mode, and last successful detective evaluation.
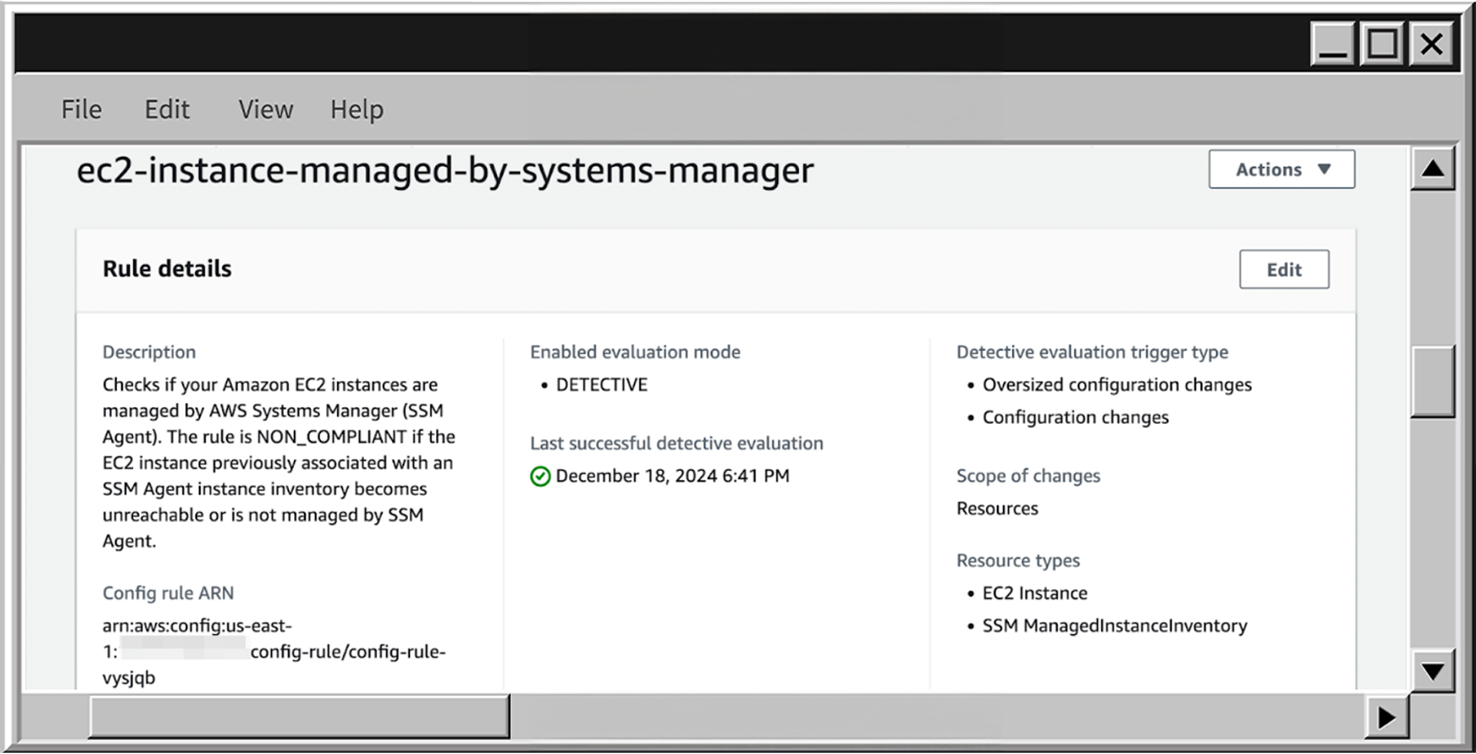
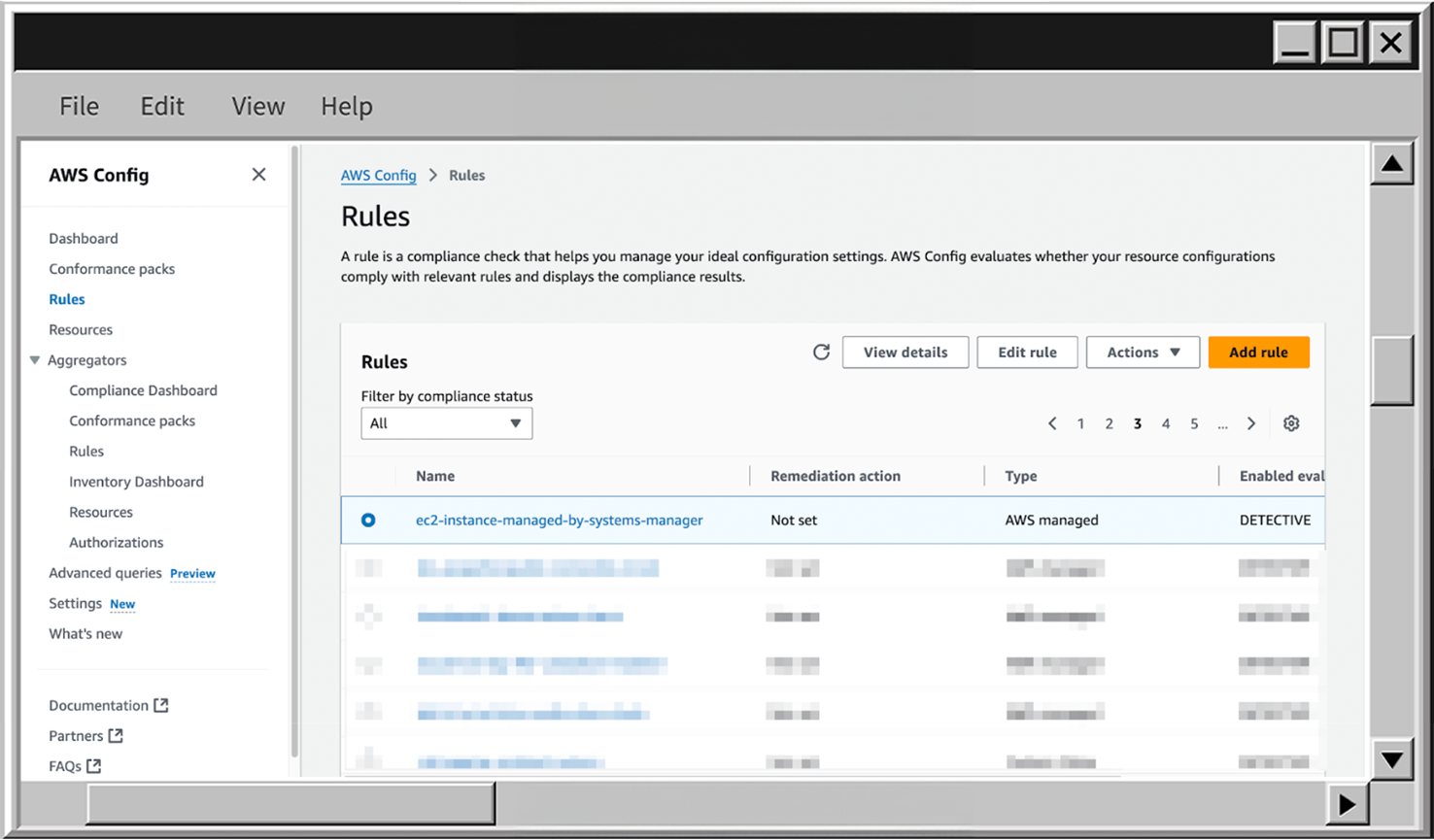
- To view the resources AWS Config detected and their compliance status, scroll down to the Resources in scope section. Click Expand, then select All to see all resources associated with the rule. In my case, it lists EC2 instances with a Compliant status, meaning each instance has the AWS SSM agent configured and available.
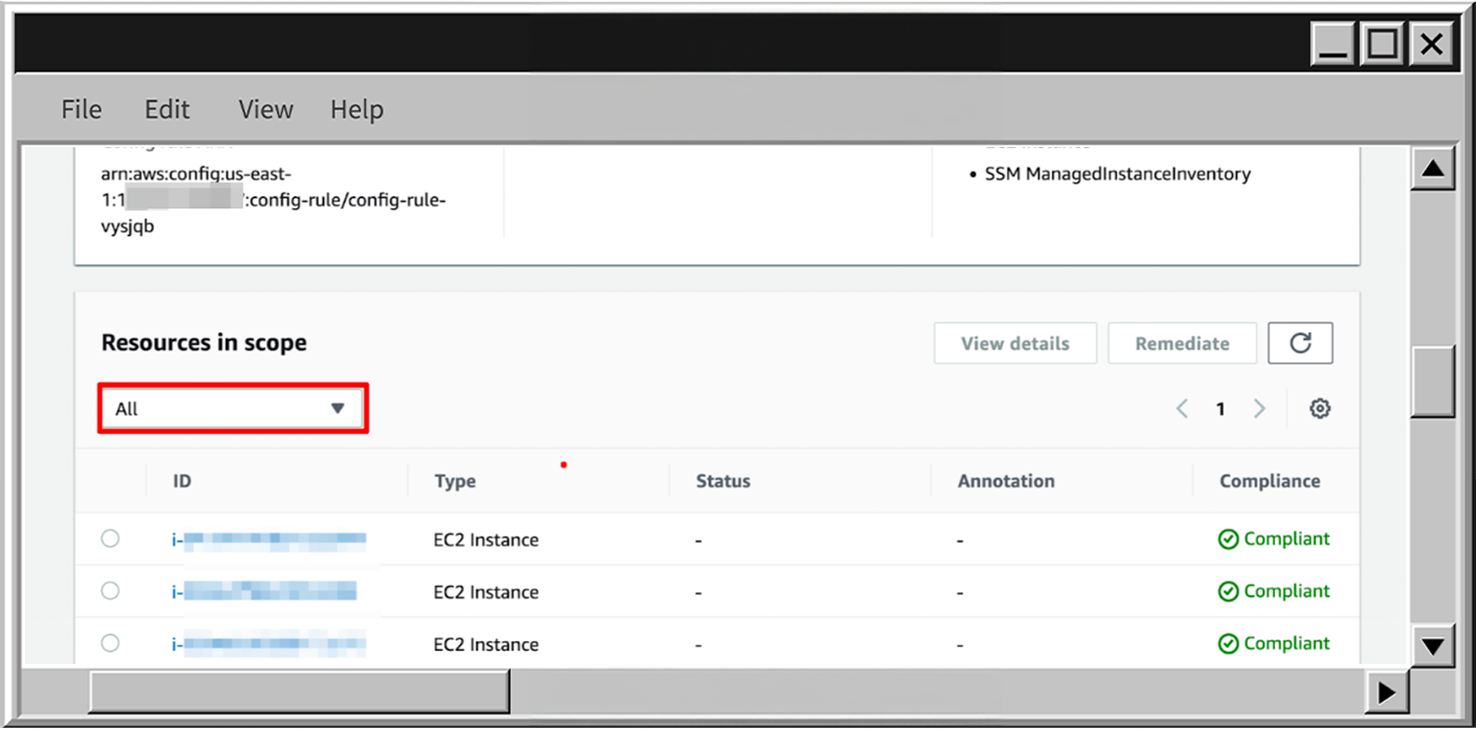
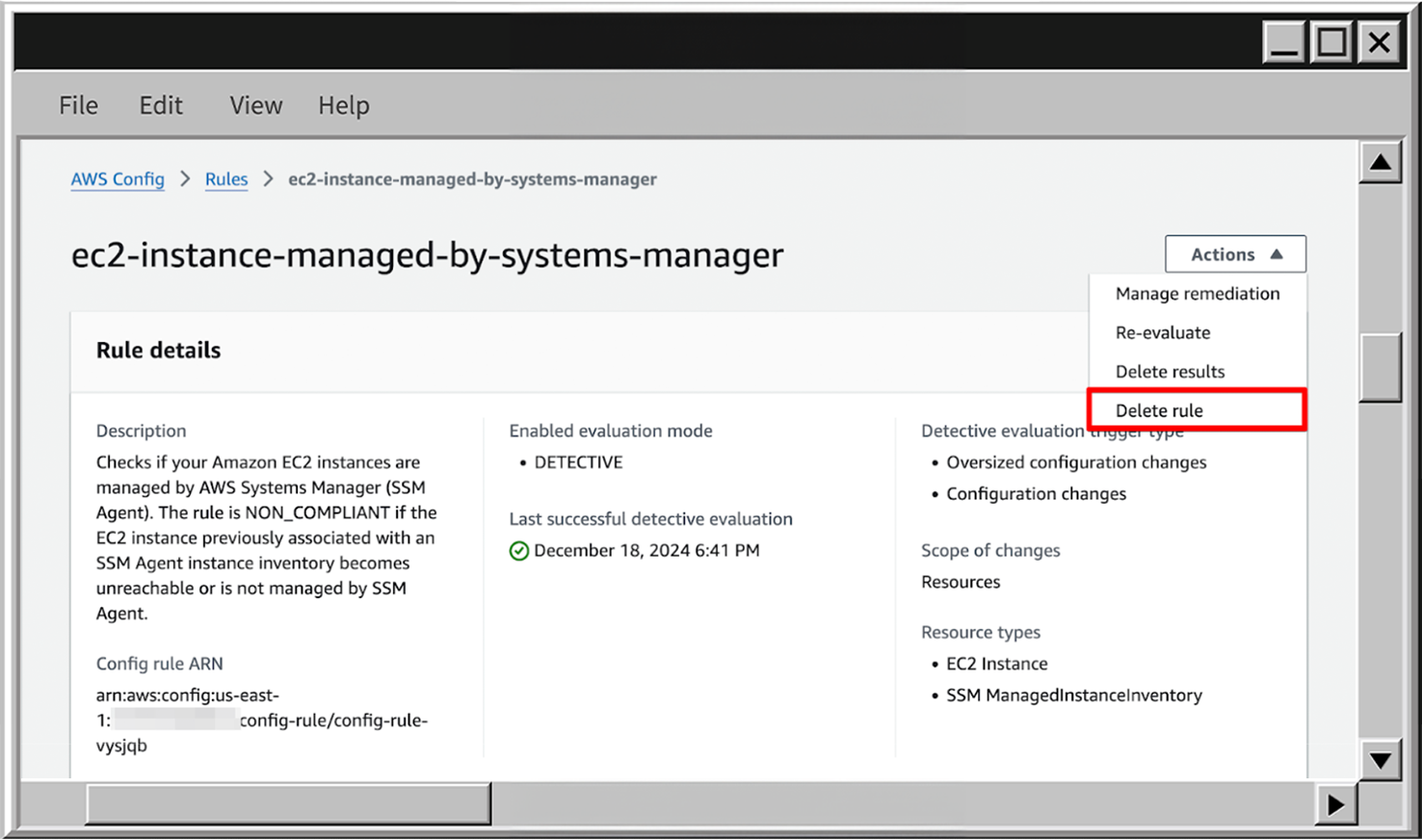
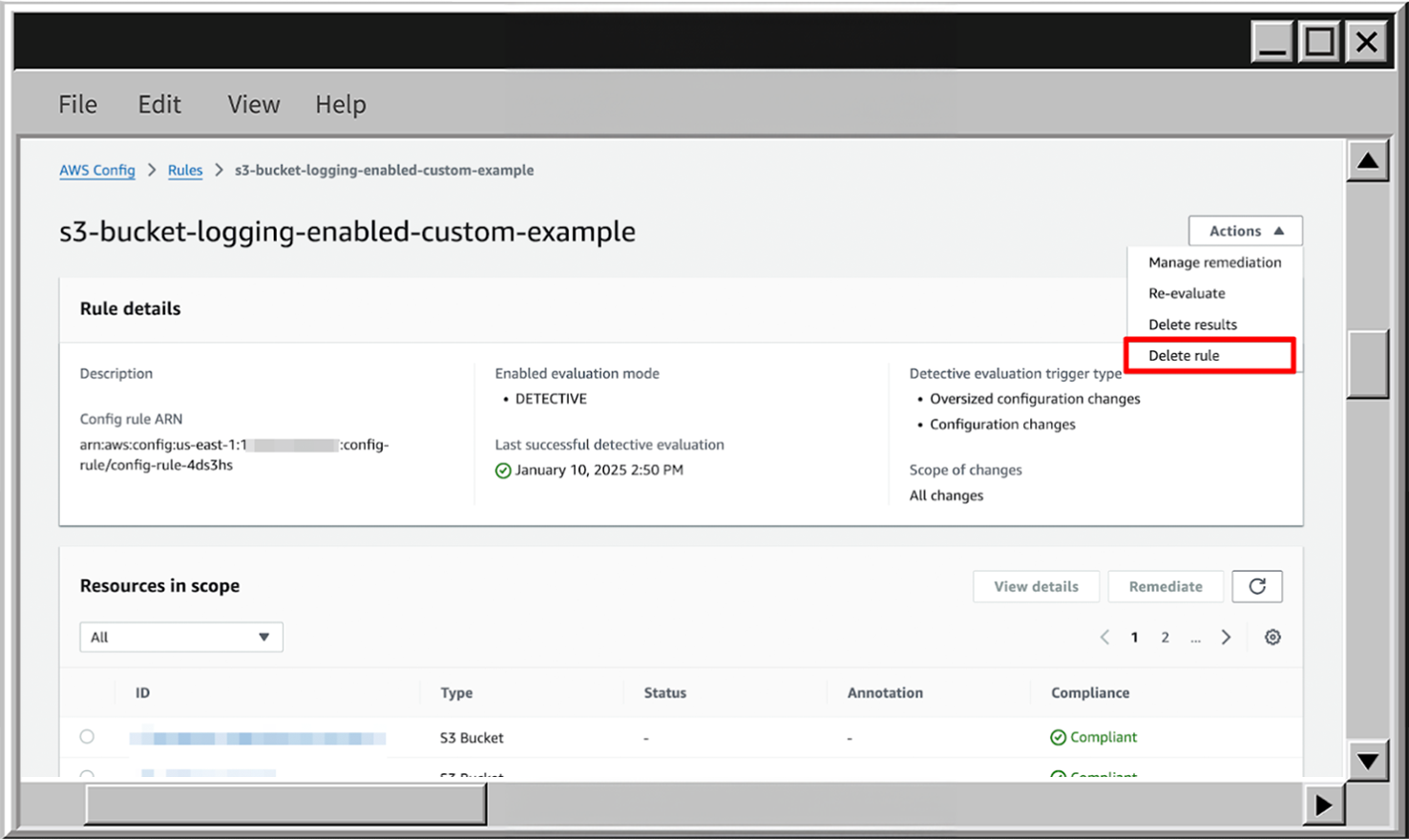
- To delete the rule, scroll up, click on Actions expand, and choose Delete rule.
Custom AWS Config Rules
Now let’s dive deeper into custom AWS Config rules, which help address specific scenarios.. In my case, I will create a CF Guard policy to define the custom AWS Config rule.
- To create Custom rule, identical to Managed AWS Rules go to the Rules section and click on Add rule.

- Now choose Create custom rule using Guard and go to the next Step.
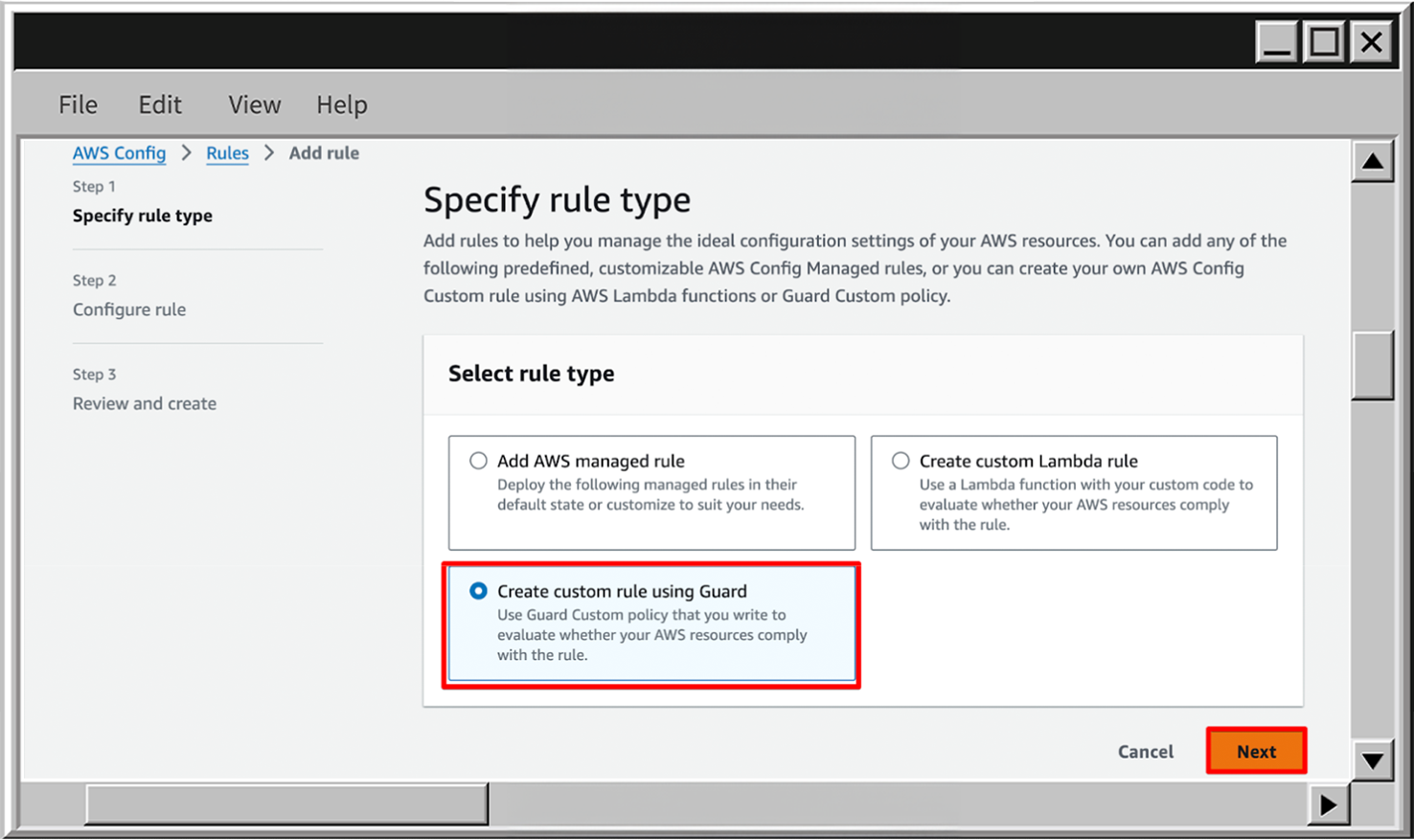
- Add rule name, scroll down to the Rule content and put the following rule. It will check for bucket logging only for buckets which doesn’t contain the log in the S3 bucket name.
rule S3BucketLogging
when configuration.name != /.*log.*/ {
supplementaryConfiguration.BucketLoggingConfiguration.destinationBucketName is_string
}- When the rule is created, find it on the Rules page and check the findings. In my case, it looks like this:
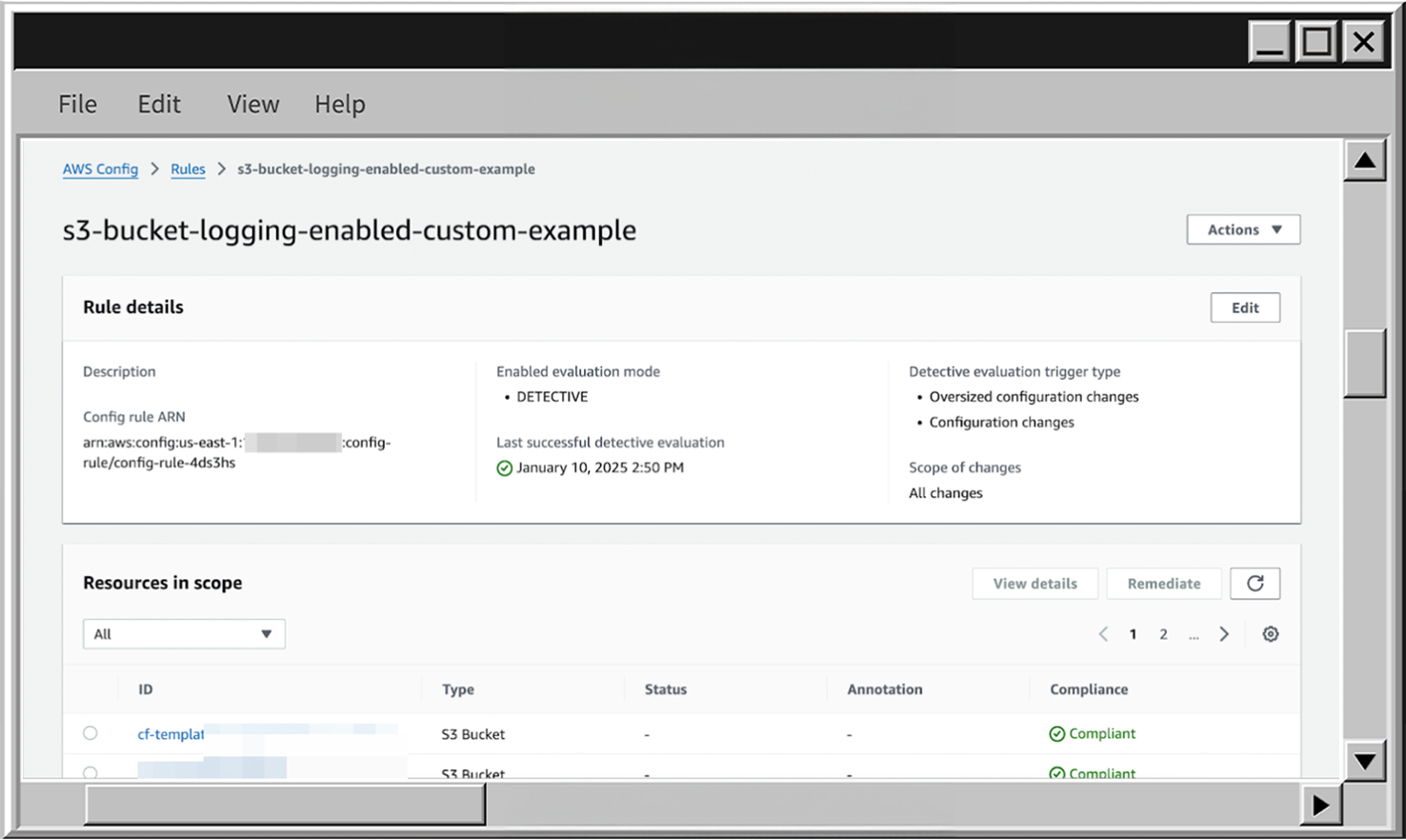
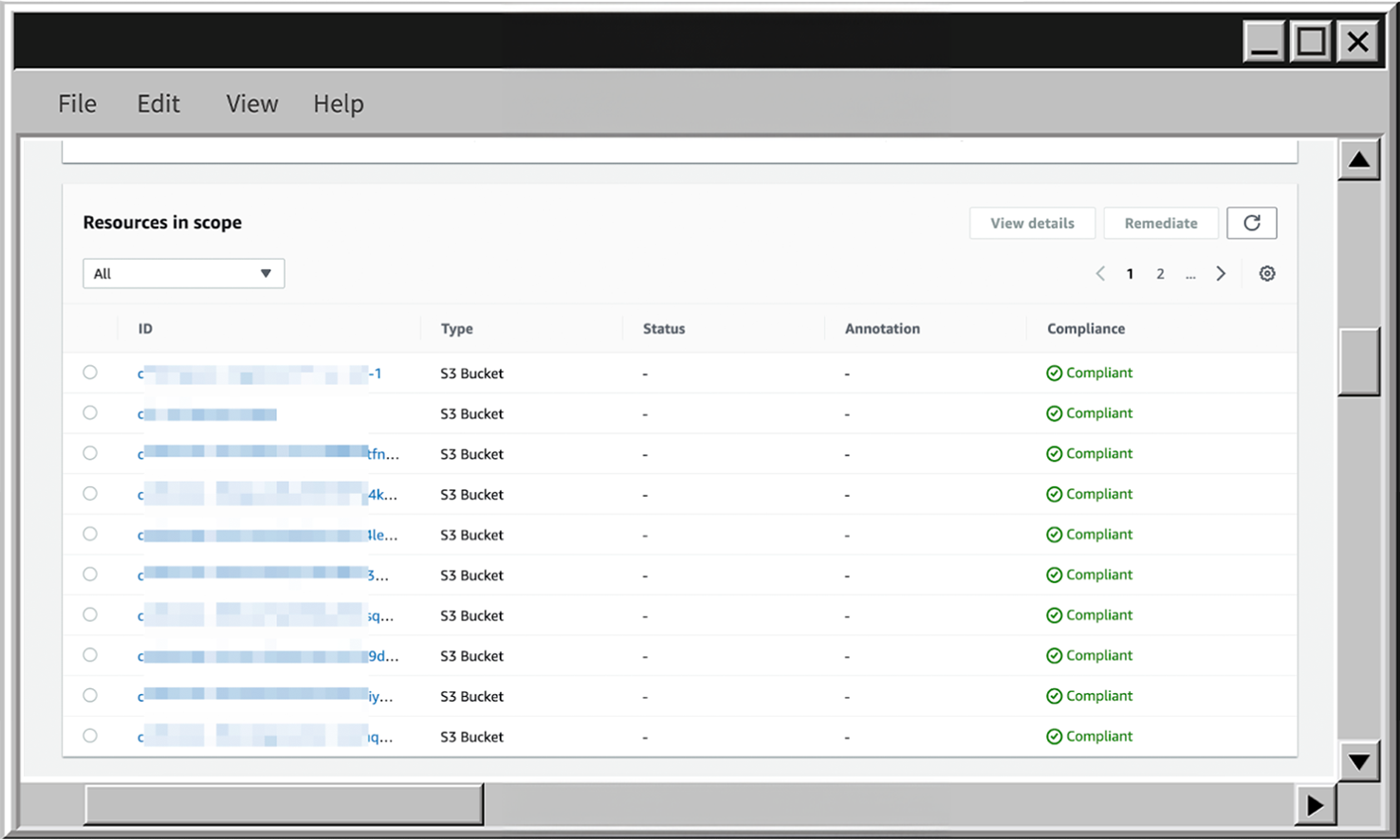
- To delete the rule scroll up, click on Actions expand and choose Delete rule.
AWS Config Conformance Packs
Organizations often need multiple AWS Config rules, and Conformance Packs provide a convenient way to group and manage them. These packs are essentially CloudFormation templates and stacks. If you're familiar with CloudFormation, setting up a template with all the necessary rules will be quick and straightforward. This also gives us two ways to create AWS Config rules in bulk:
- Via AWS Config Conformance packs
- Via AWS CloudFormation
Conformance packs will have more features in comparison to managing rules using AWS CloudFormation:
- Conformance Packs have a dedicated dashboard that provides compliance summaries for the entire set of rules. This makes it easier to track and report compliance status without needing additional custom software.
- Conformance packs can be deployed from one place to manage the rules across the entire organization
- We can see the compliance history for all Conformance packs
- With Conformance packs rules are grouped in AWS Config, which is more convenient for querying and reporting
- We can get and filter the rules by their status and name on Conformance pack page without using the Advanced queries
Drawbacks of Conformance Packs
One drawback is that AWS additionally charges for it. For detailed pricing, check the AWS Config Pricing page. So, if you don’t need the features described above you can feel free to manage everything directly using the CloudFormation stacks.
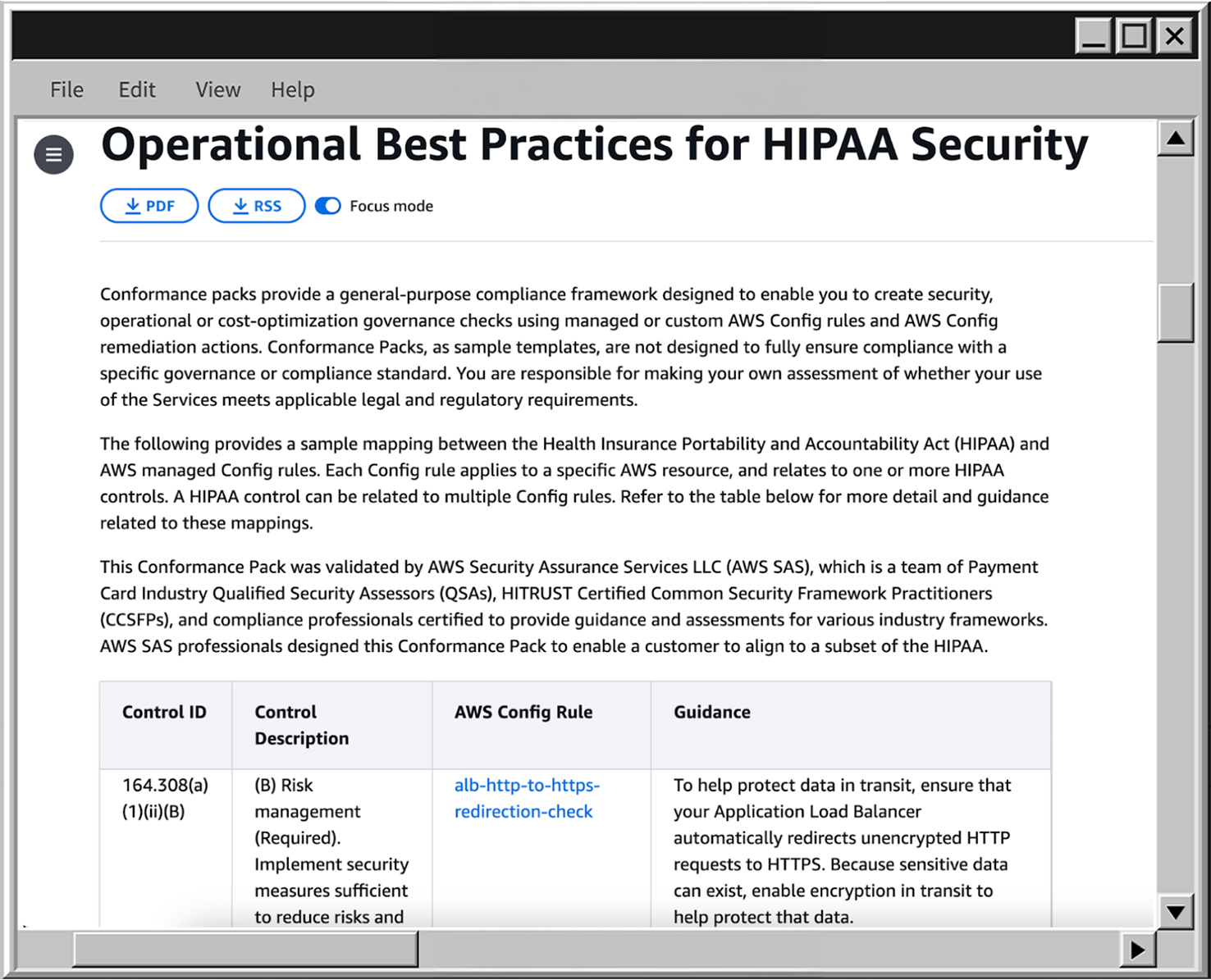
Also, AWS provides a large amount of Conformance pack templates, which can be a great starting point to create your own set of rules to fulfill the project requires. For example, if you open the template for HIPAA, you can see the list of rules and controls covered by these rules, as well as high-level guidance for each.
All templates are available in the official AWS repository.
Instruction
Now let’s try to create a conformance pack using one of the ready-to-use templates - Operational Best Practices for HIPAA Security:
- In AWS Config service go to the Conformance packs page and click on Deploy conformance pack.
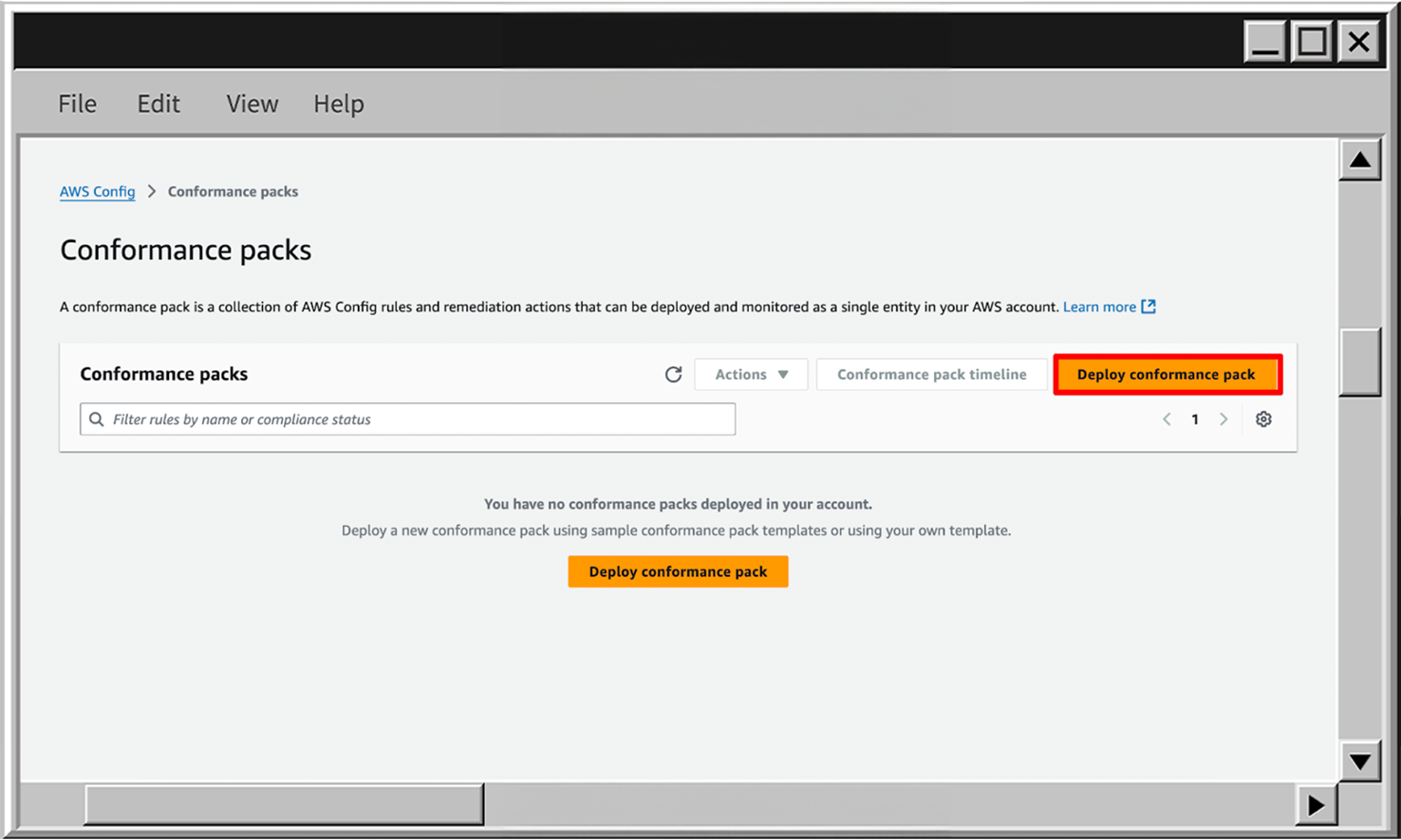
- On the next page, choose the Use sample template and find the sample template - Operational Best Practices for HIPAA Security.
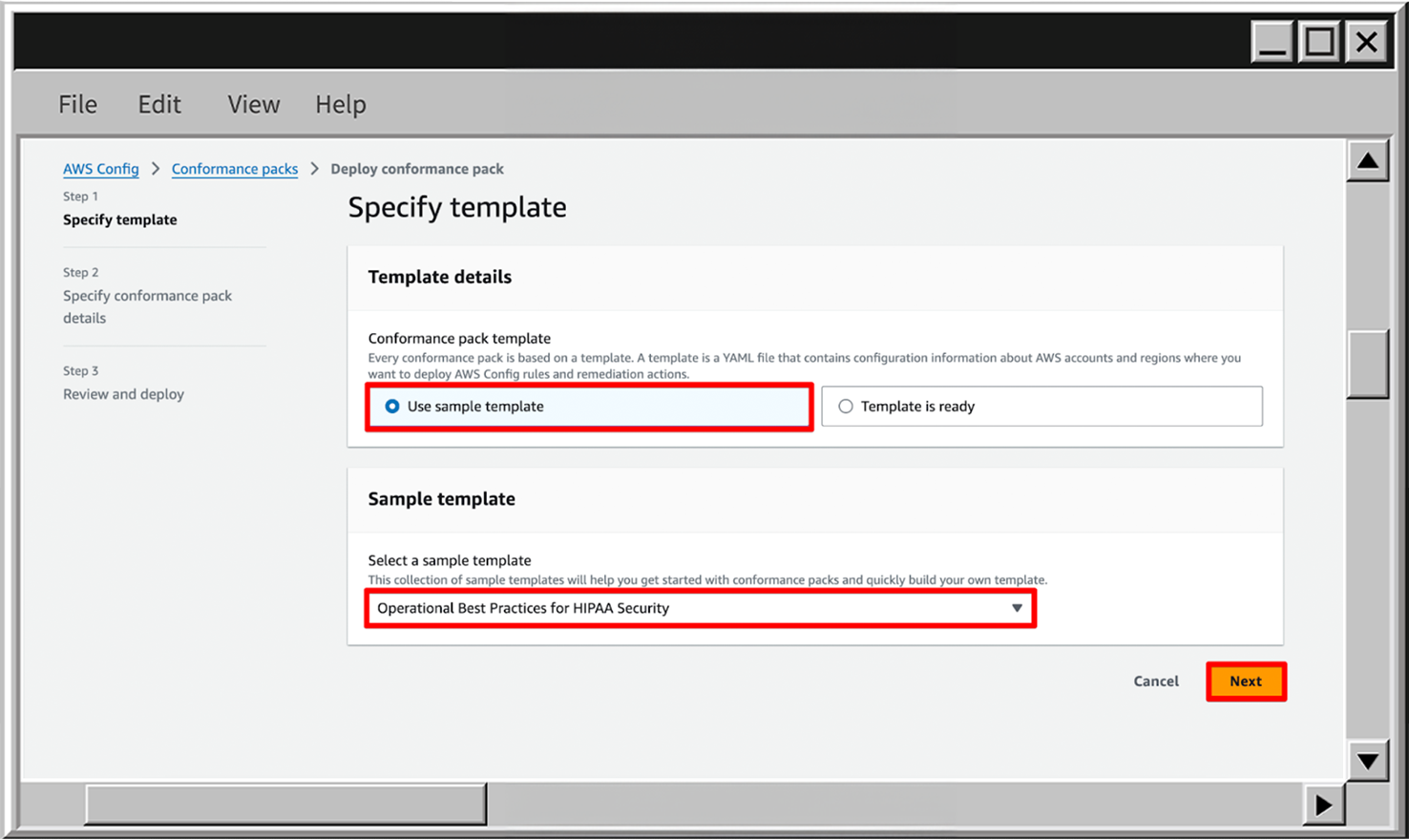
- On the Conformance pack details page set the Conformance pack name. Also, you can see that the input parameters are available, but currently you don’t need to specify them, so just skip this section and go to the next page.
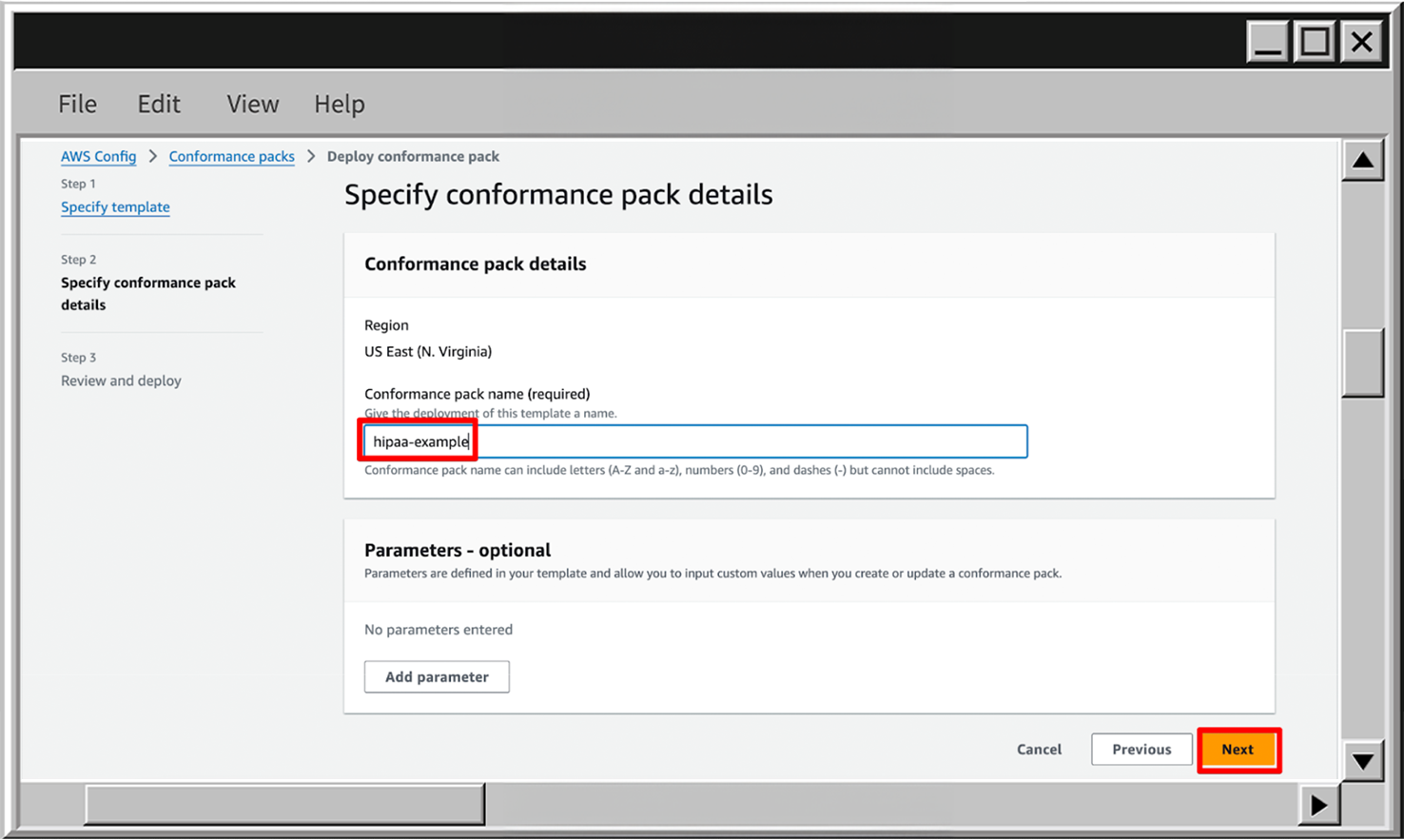
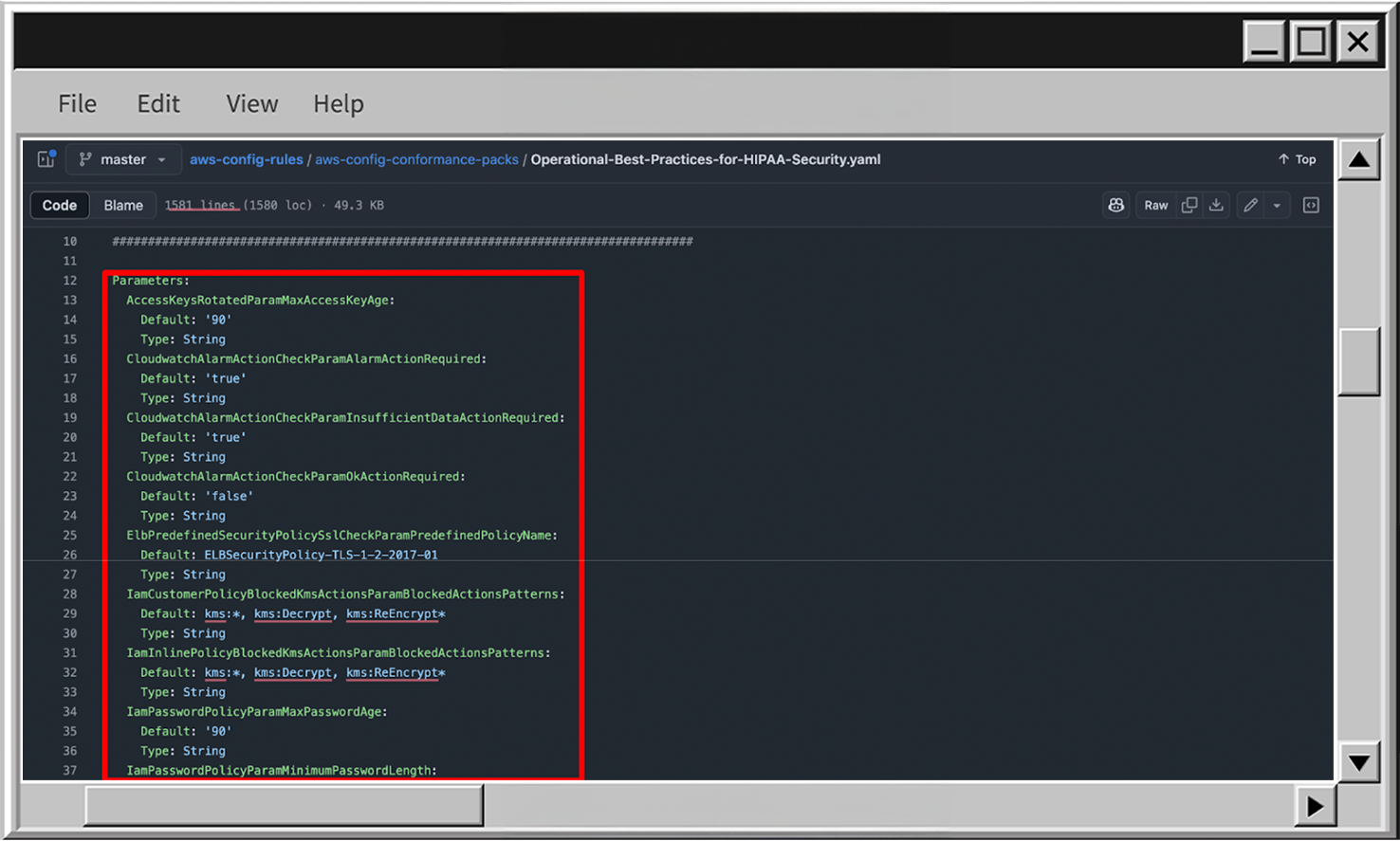
- In case you need to find out the available input parameters, you can always find these Conformance pack templates in AWS docs and check the Parameters section, for example:
- On the Review and deploy page click on Deploy conformance pack to finish the creation

- After a few minutes, you will see the deployment status as Completed, now you can open the Dashboard by clicking on the pack name

- On the dashboard page we can see the:
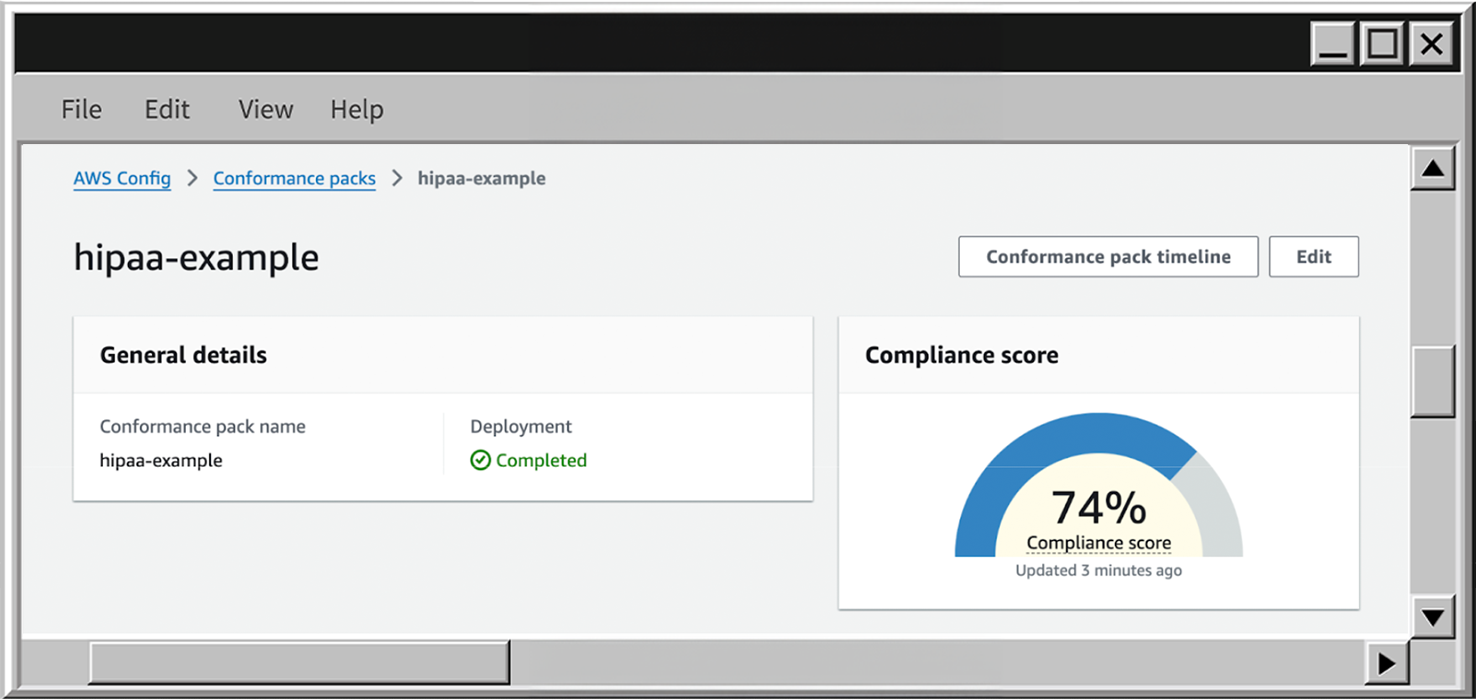


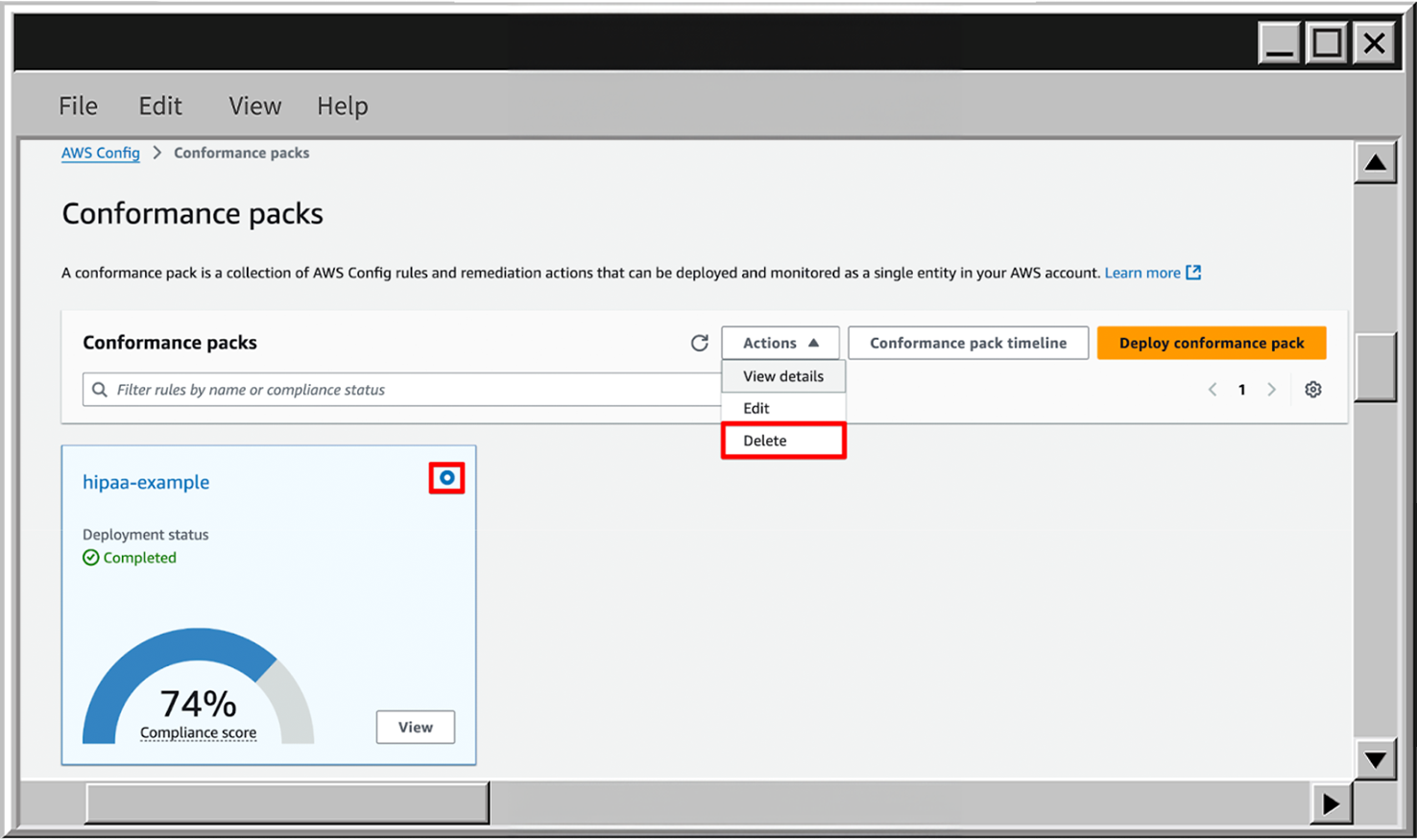
To delete the conformance pack, just to the Conformance packs page, choose the necessary pack, click on Actions and then Delete
Summary
AWS Config is a great tool for keeping an eye on your AWS resources and making sure everything stays compliant. In this guide, we covered most of the parts to get started with AWS Config:
- Setting up AWS Config and enabling resource tracking.
- Using both managed and custom rules to enforce compliance.
- Managing compliance efficiently with AWS Config Conformance Packs.
By leveraging AWS Config, you can detect changes, enforce policies, and prevent compliance issues before they escalate - all without the need for additional custom tools. Whether you're working with a few rules or managing compliance across multiple AWS accounts, AWS Config helps keep your environment secure, auditable, and under control.







.png)
.jpg)
.webp)